Features
Collect & Monitor Config Changes Across Your Entire Infrastructure
Collect & Monitor
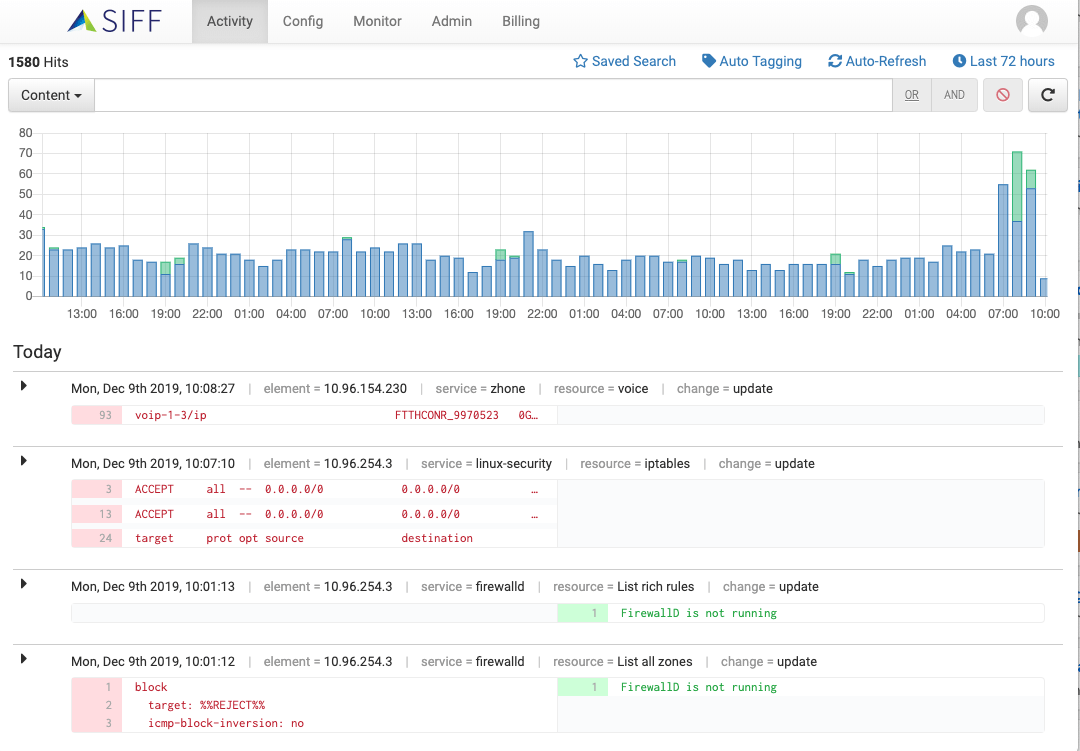
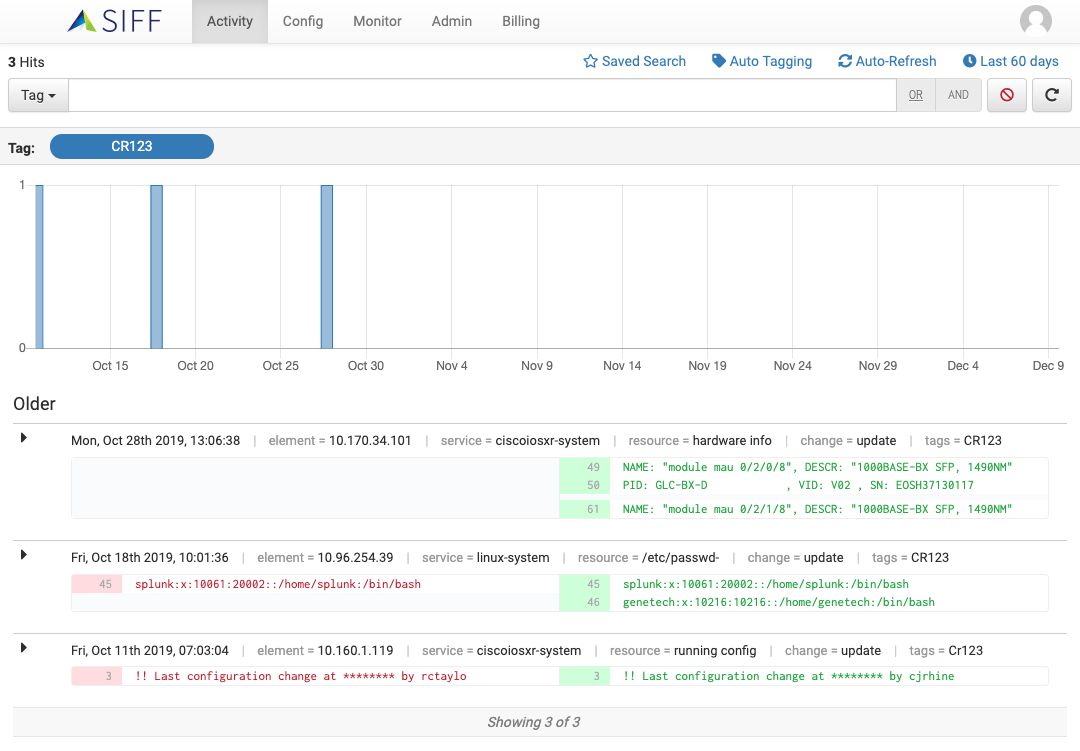
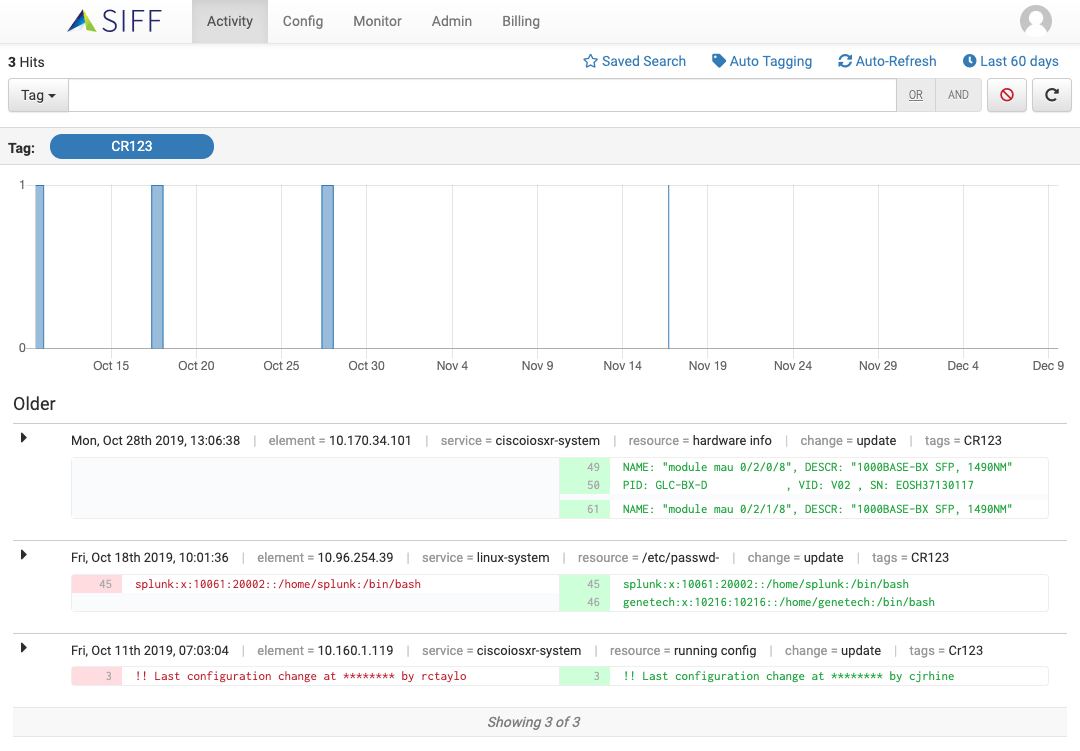
Change Activity Stream
Change Activity Bar
Activity Bar chart indicating volume of new and updated configs over time
Full Visibility to Changes Across IT Infrastructure
Visibility to config changes across all domains and functional groups – applications, servers, networks, storage, VMs, cloud, containers, etc
Collect & Monitor Any Configuration Type
Collect config files, command line outputs, MS Windows registry, database entries, APIs responses, AWS configs
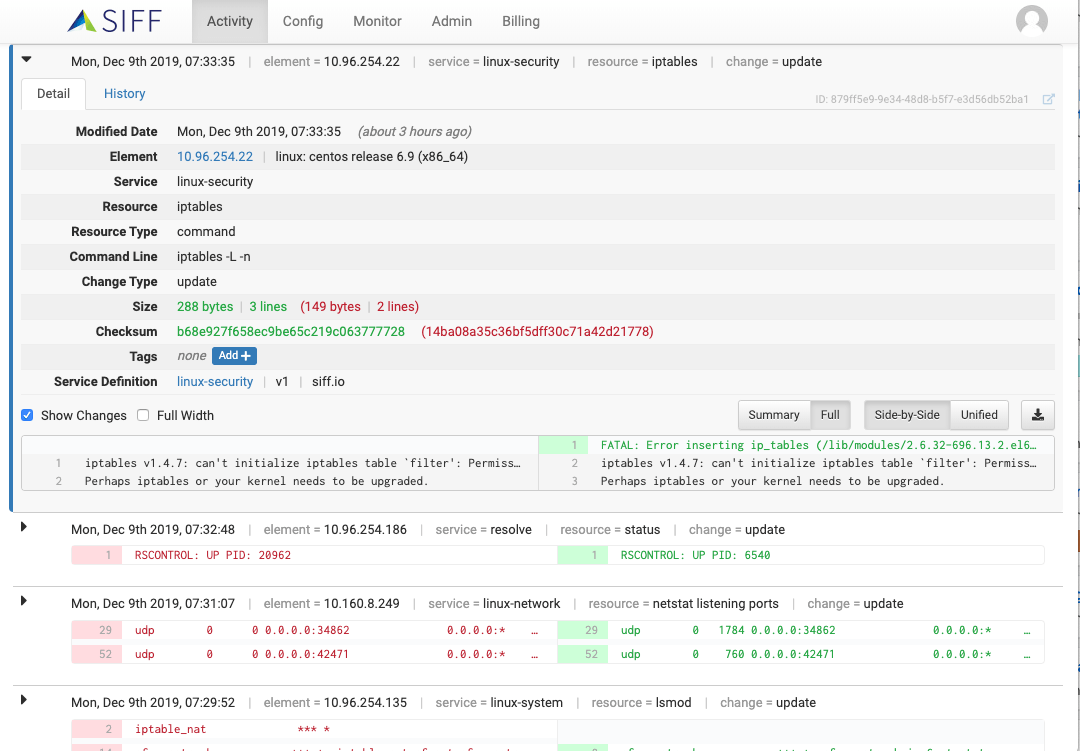
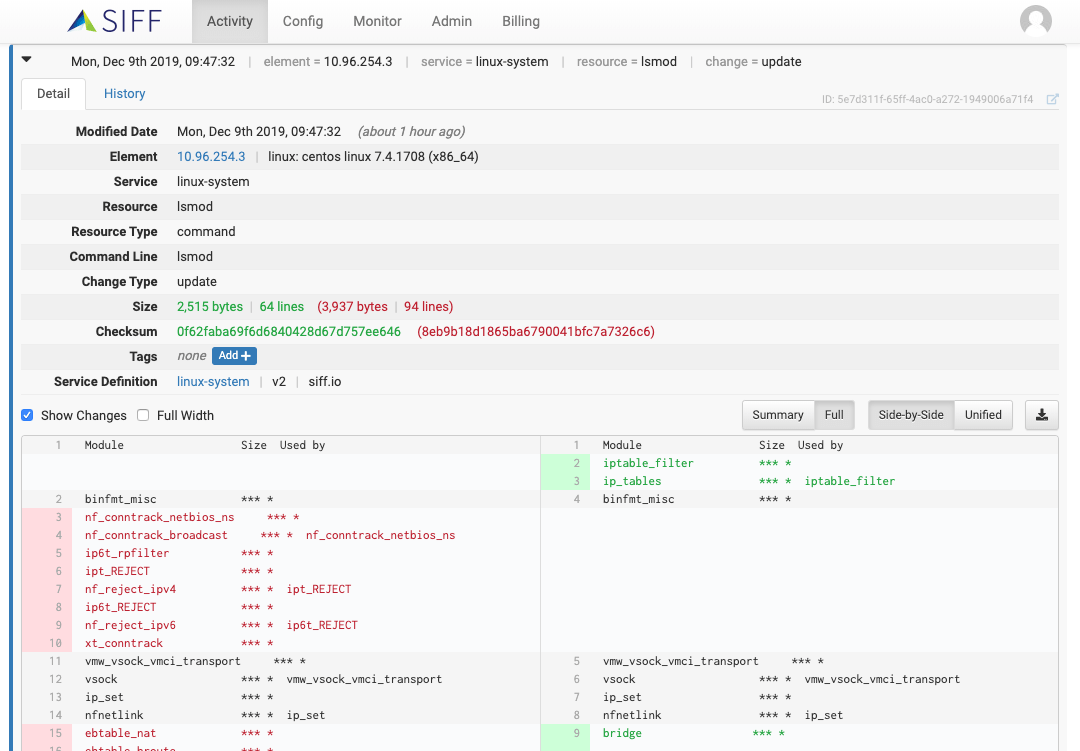
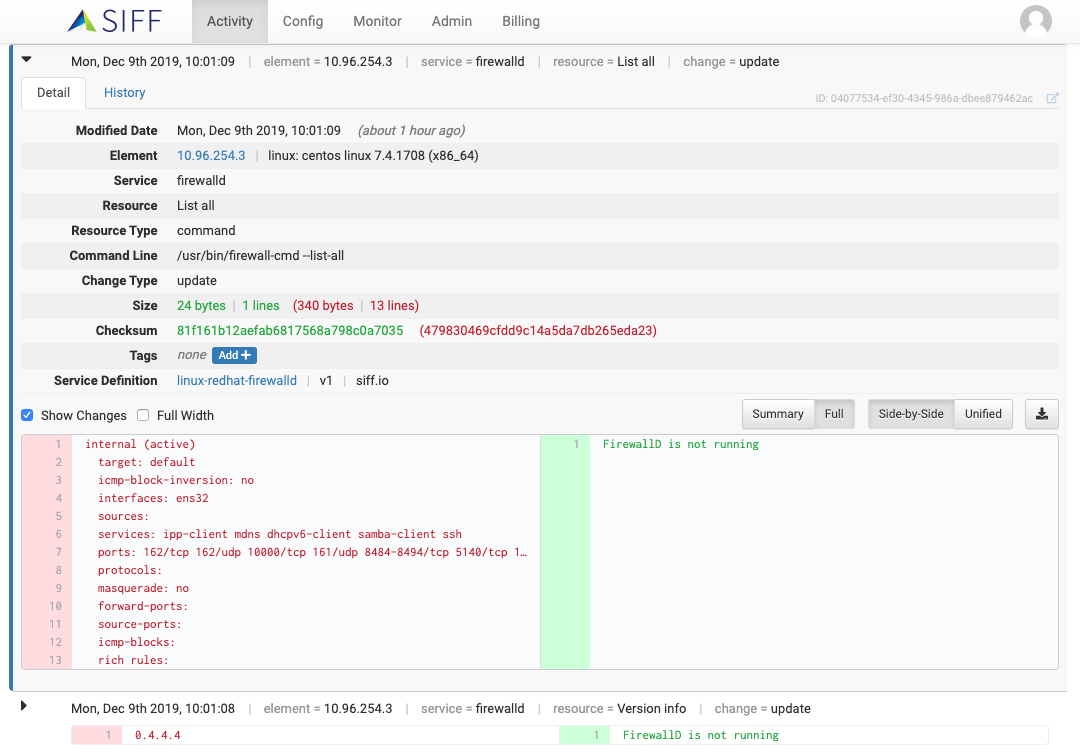
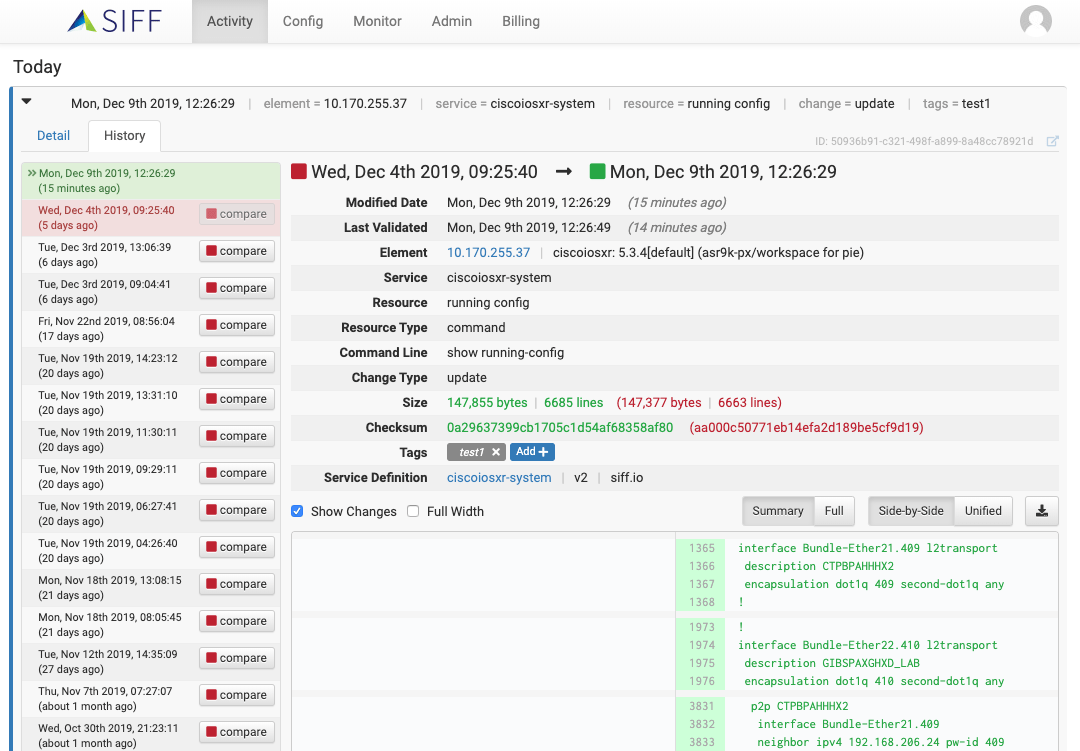
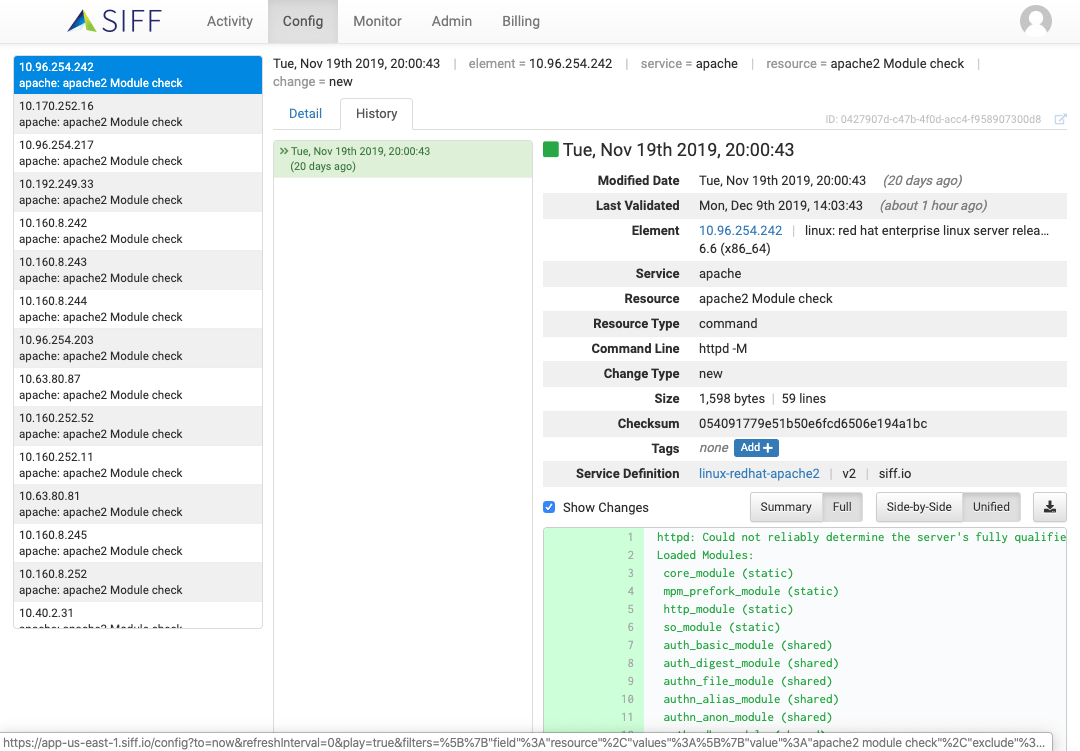
Change Detail & DIFF Views
Change Summary DIFF View
Highlight actual changes and save time to identify what has changed in the configuration
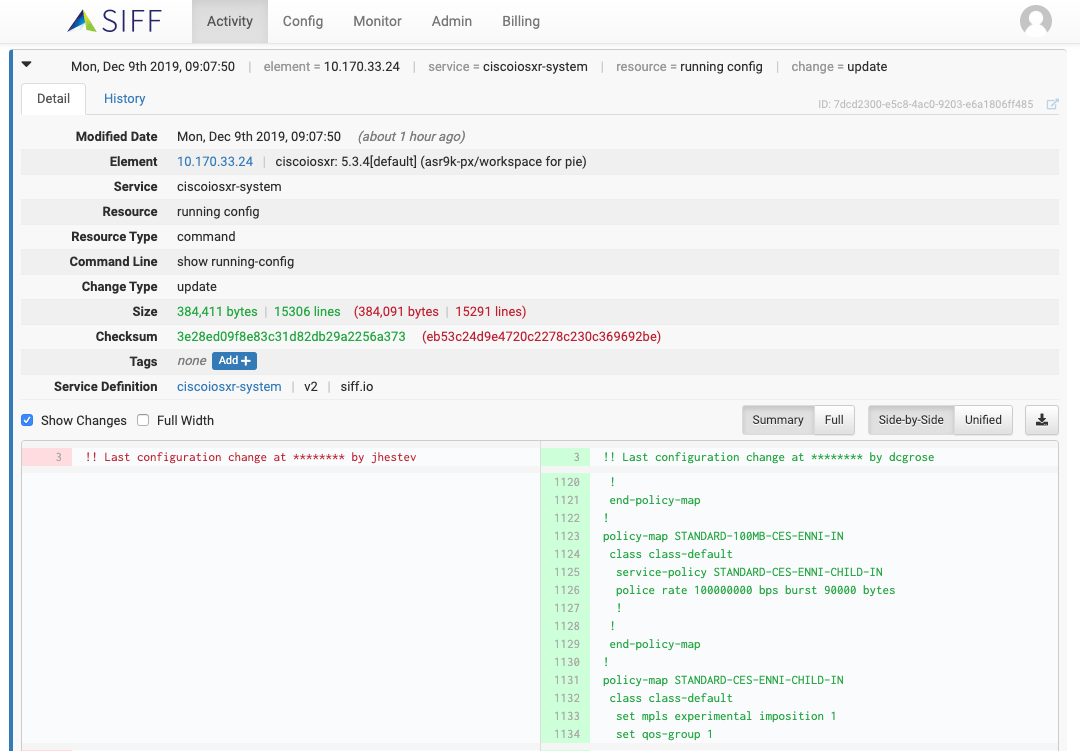
Full Configuration DIFF View
View entire configuration output and compare against configuration history and other similar systems
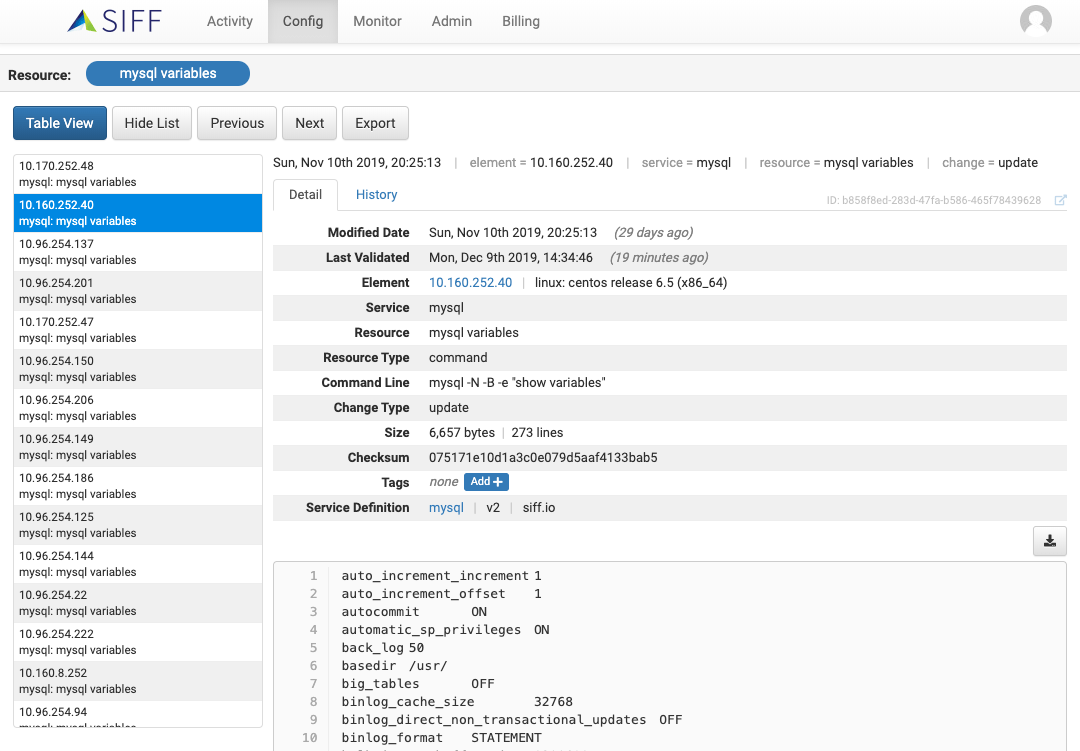
Full Configuration Download
View and download entire configuration at any point-in-time in case your existing backup does not have you covered.
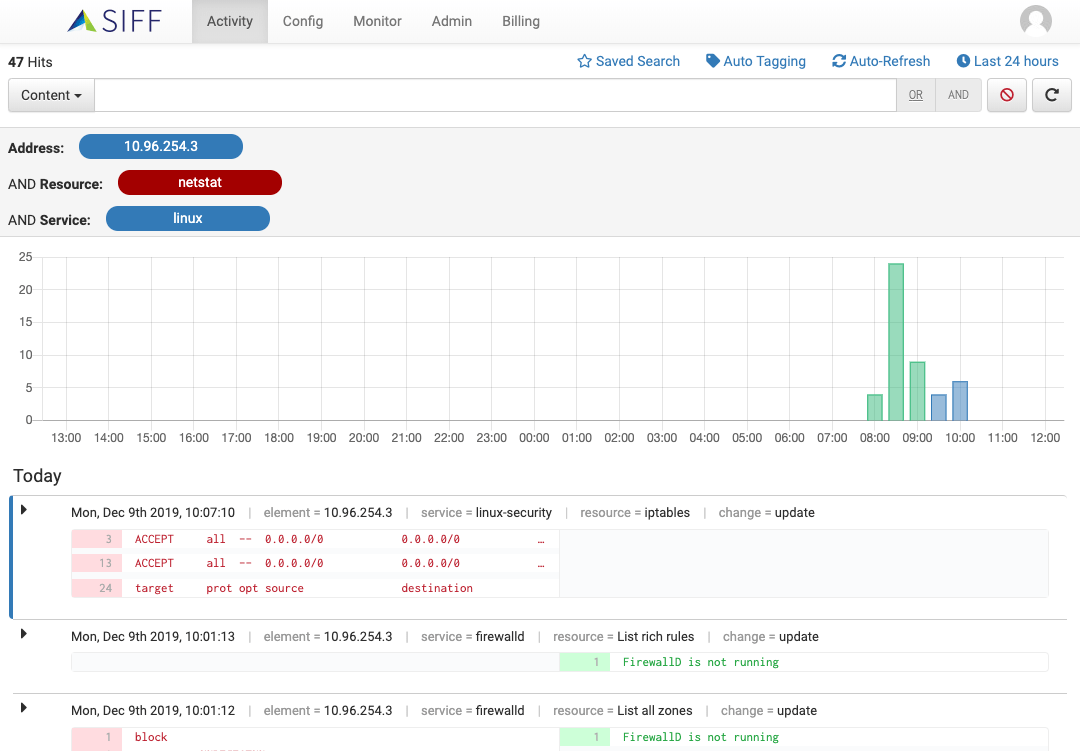
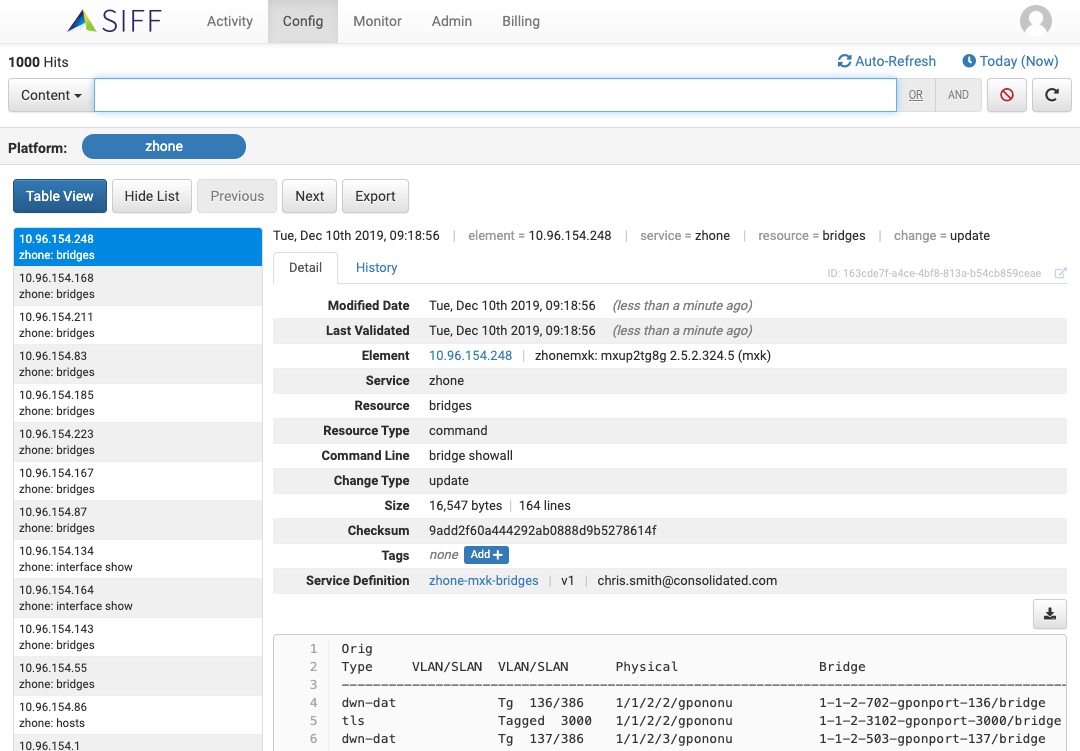
Network Config Changes
Monitor network configuration changes
Capture full configuration details and quickly identify additions / deletions to help you quickly identify problems
Automatically discovery and collect configuration
Supports common vendors such as Cisco, Brocade, Zhone and we’ll seamlessly add new ones if you’re not covered
Add your own network commands to monitor
Any device commands can be captured and monitored for changes
Server Config Changes
Monitor server configuration changes
Out-of-the-box Service Definitions to monitor server configs, services, file systems, security, kernel module, etc
Add your own files and server commands to monitor
Define your own service definitions to discovery and monitor for files, commands and registry configuration and changes
Security Config Changes
Monitor network security configuration changes
Detect firewall config and policy changes
Monitor server security configuration changes
Detect firewall config changes, kernel settings, etc
Monitor cloud security configuration changes
Detect resource security and security group policy changes
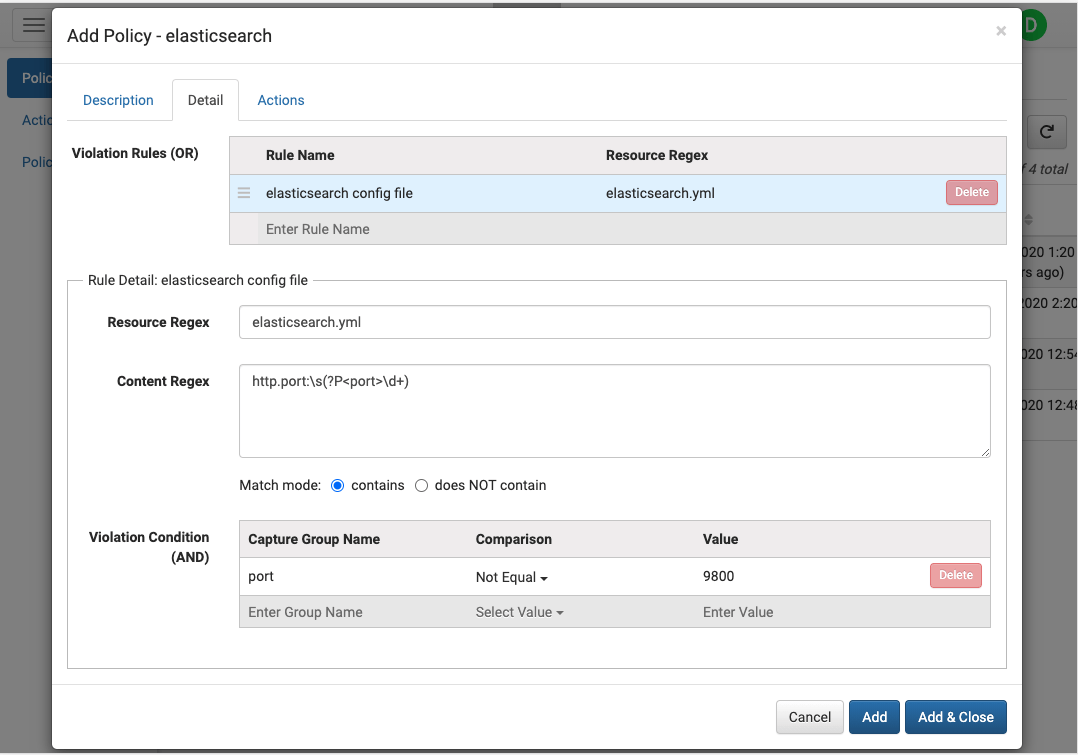
Configuration Security Policy & Compliance
Configuration Policy Monitor
Analyze all config changes to ensure policy compliance
Continuously examine all configuration changes against defined policy rules to alert or take action upon policy violations.
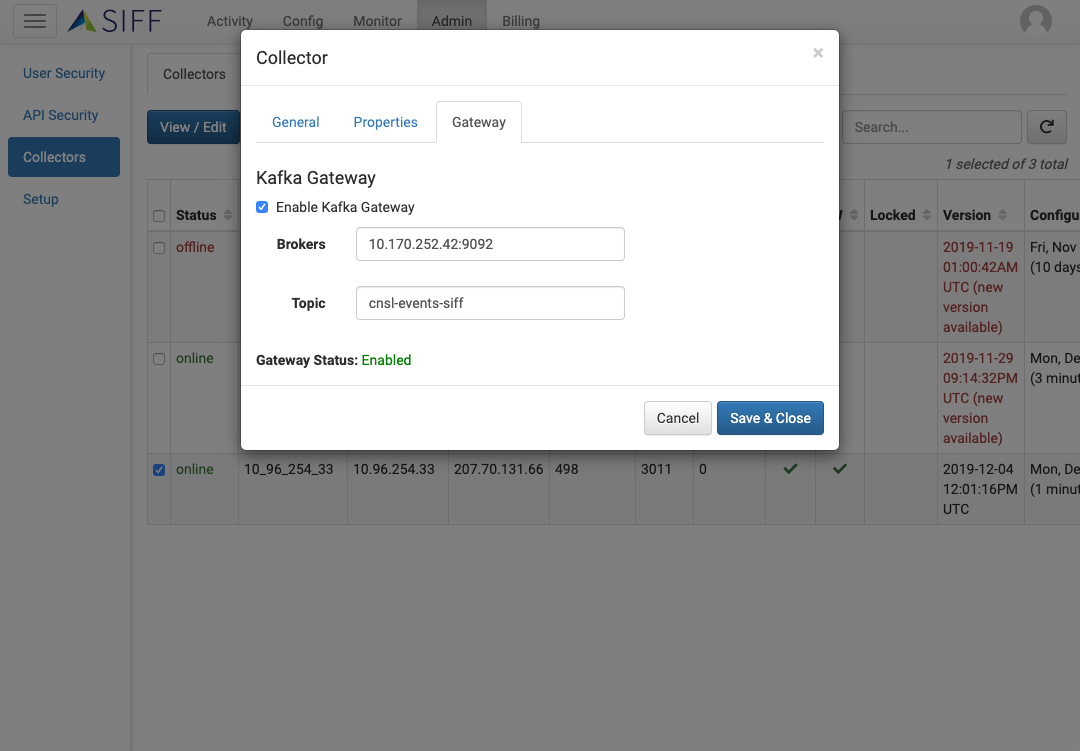
Integration with SIEM, Fault Mgmt or ITSM systems
Integrate with your management systems to take action on policy violations. Includes the actual change details and highlights what was changed.
Search and Report on Policy Violation Changes
Search config change activity that violates Policy Rules
Easily search change activity to find configuration changes that violates Policy Rules.
Generate Audit and Compliance Reports
Generate reports for audit and compliance reviews.
Review Planned vs Unplanned Changes
Review planned and unplanned changes to identify gaps in Policy Rules coverage.
Configuration Validation Automation
Comparing device running-config vs startup-config
Verify integrity of device configs by ensuring the startup configs are consistent with the current device configs.
Comparing configs between components in a cluster
Verify the configuration are consistent across devices within a cluster.
Reduce & Prevent Incidents
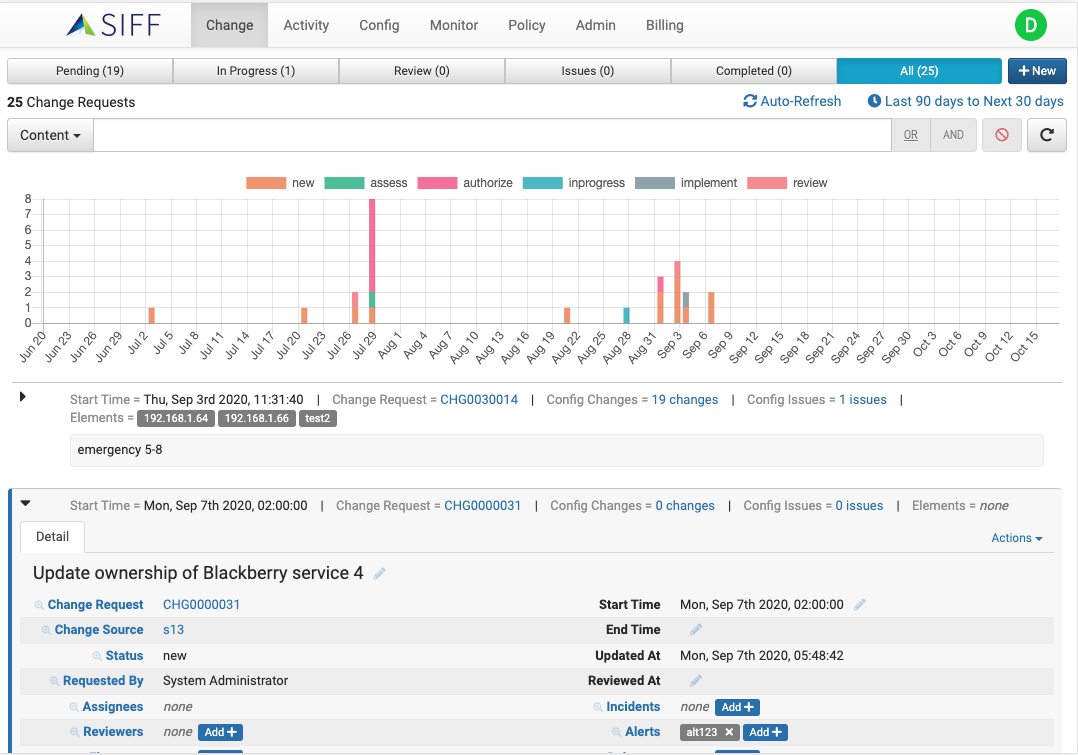
Change Horizon
Operational Change Dashboard across multiple ITSM systems
Provides an operational view of all current, pending and recently completed change requests in your environment across multiple ITSM change management systems.
Bi-direction integration with ITSM system
Integrate with your Change Request systems such as ServiceNow, to seamlessly associate Change Requests with configuration changes.
Prevent Incidents by Reviewing CR Config Changes
Automatically tag config changes with Change Request ID
Config changes are automatically annotated with Change Request ID so you can see what changes were made by a Change Request for review or troubleshooting
Enable peer-review of completed change requests
Reviewers are automatically notified and can easily check results of completed change requests to ensure correctness, any manual errors or unexpected impact – all without requiring any manual documentation
Planned vs Unplanned Configuration Changes
Unauthorized config changes
Monitor change activity and identify ad-hoc or unplanned changes which are often the cause of many incidents and outages
Identify anomalies and potential security IOC
Correlate security alerts with configuration changes to help accelerate security forensics and analysis.
Search for Changes Resulting from Change Requests
Search for config changes by Change Request
Quickly search for config changes for a Change Request either by searching for the Change Request ID or via UI integration
Track config changes for complex Change Requests
Changes may be individual changes to specific devices or part of a larger service rollout involving many CRs
Identify planned, unplanned and unauthorized config changes
Improve the quality and confidence of your change management processes
Troubleshoot & Repair
Troubleshooting Root-Cause
Reviewing Related Configuration Changes
Isolate and identify the root-cause by examining possible configuration changes that caused the problem rather than just relying only on alert and performance symptoms
Adjust time range and search criteria
Reduce the search-space by adjusting the time range, related devices, services and recent recent Change Request work
Triage Change Detail & History
Pin-point Adds & Deletes to configuration changes
Quickly identify relevant changes, especially with extremely large configurations, allowing you to focus on finding the root-cause
View and compare change history revisions
View configuration changes in the past and compare the differences between any specific versions
Collaborate and share tags and links to change entries
Complex incidents often involve multiple teams and different perspectives. SIFF collects data across all silos and allow users to easily share and cooperatively work on problems
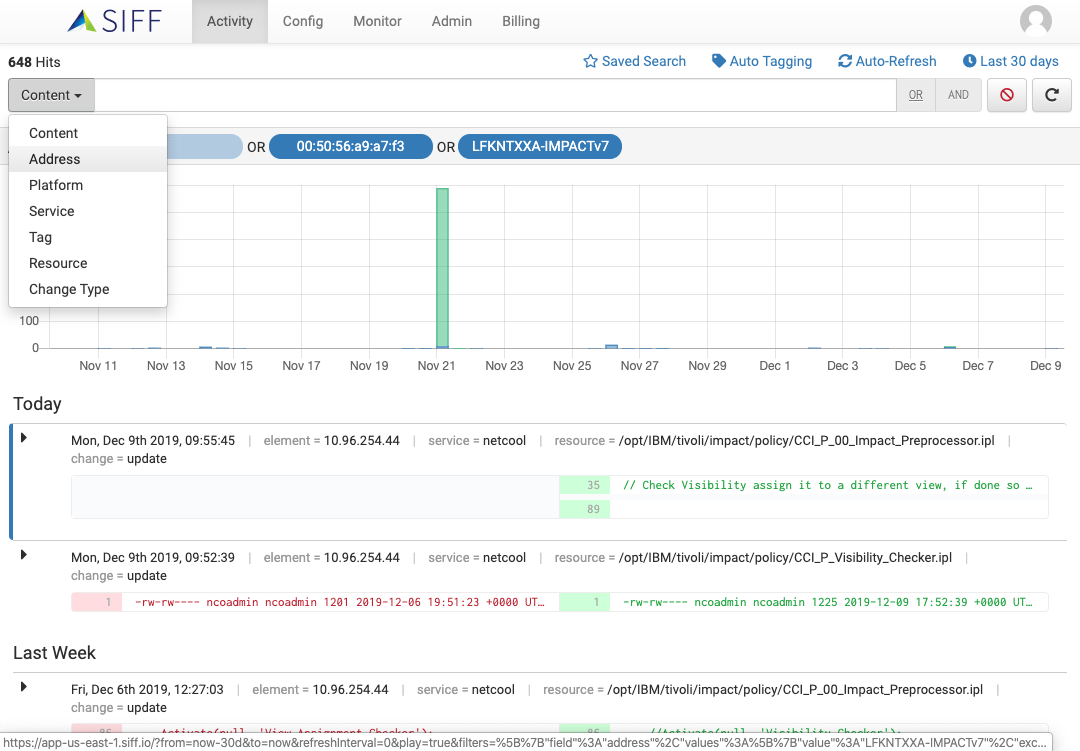
Intelligent Search Categories
SIFF goes beyond just field text searches
Intelligent search categories makes it easy by doing the leg work for you. For example, the Address category supports multiple types of addresses (IPv4, IPv6, DNS, hostname, MAC, etc). It even resolves DNS names to multiple IP address to find the relevant config changes
Change Requests Related Configs
Identify configs related to a Change Request
Search on Change Request IDs to quickly find related configuration changes for the completed work
Enrich your Change Request records with actual configs
Add links to your change management tool to easily find actual configuration changes for the change request
Event & Incident Management Integration
Correlate your alerts with config change events
Send configuration change events to your event management system to help correlate alerts
UI Navigation and Integration
Navigate from your alerts or tickets to SIFF to quickly triage and identify root-cause for complex problems
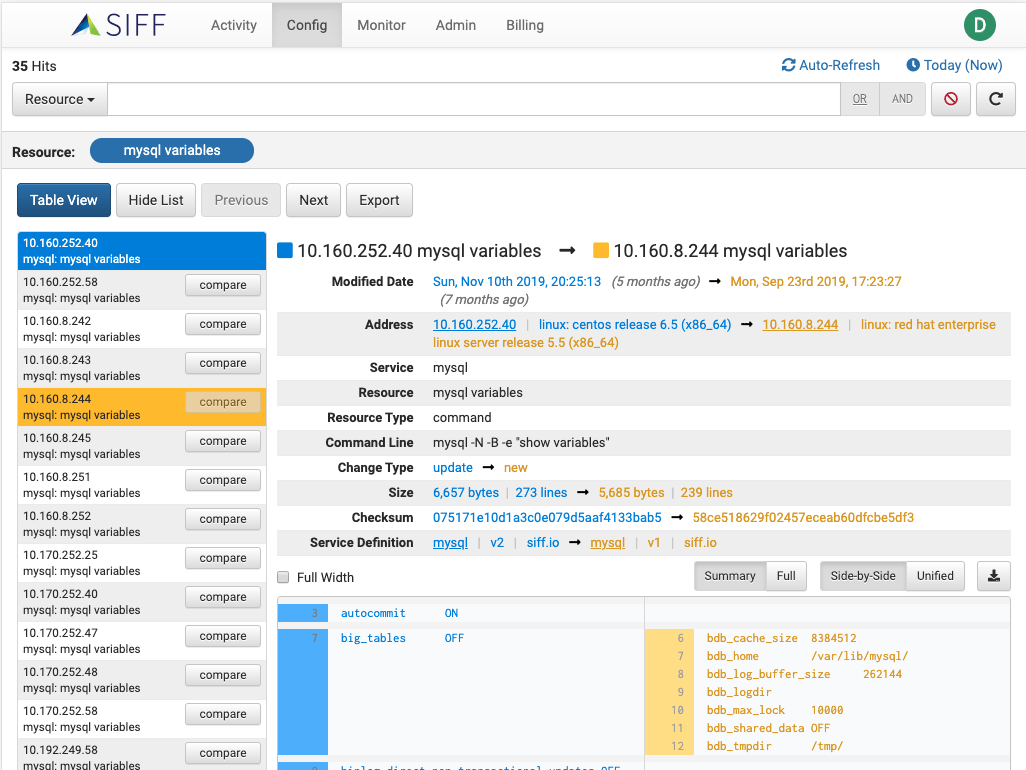
Config Search
Configuration Search
Search configs without device access
Quickly search configuration settings without logging into devices and systems
Compare configs between servers and devices
Compare configuration between different server instances and devices
Audit, Report and Export detailed configurations
Generate reports for asset, compliance and security reviews with values extracted from actual configuration details
Reporting and API Integration
Configuration Reporting / Export
Search and export configuration data
Search, view and/or export configuration data for reporting by third-party tools
Search and generated detailed reports from unstructured configuration data
Search, filter, extract and export using actual values with the configuration data
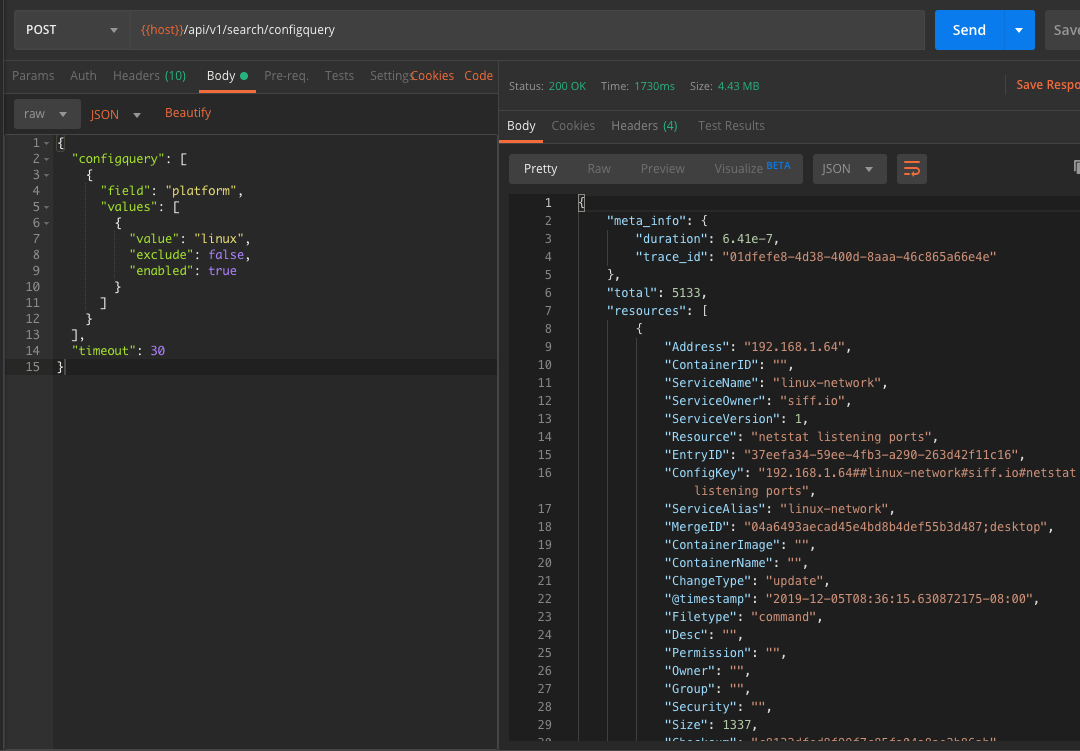
API Integration
API Services to query configuration and change information
Simple APIs with built-in examples to search for config and change data
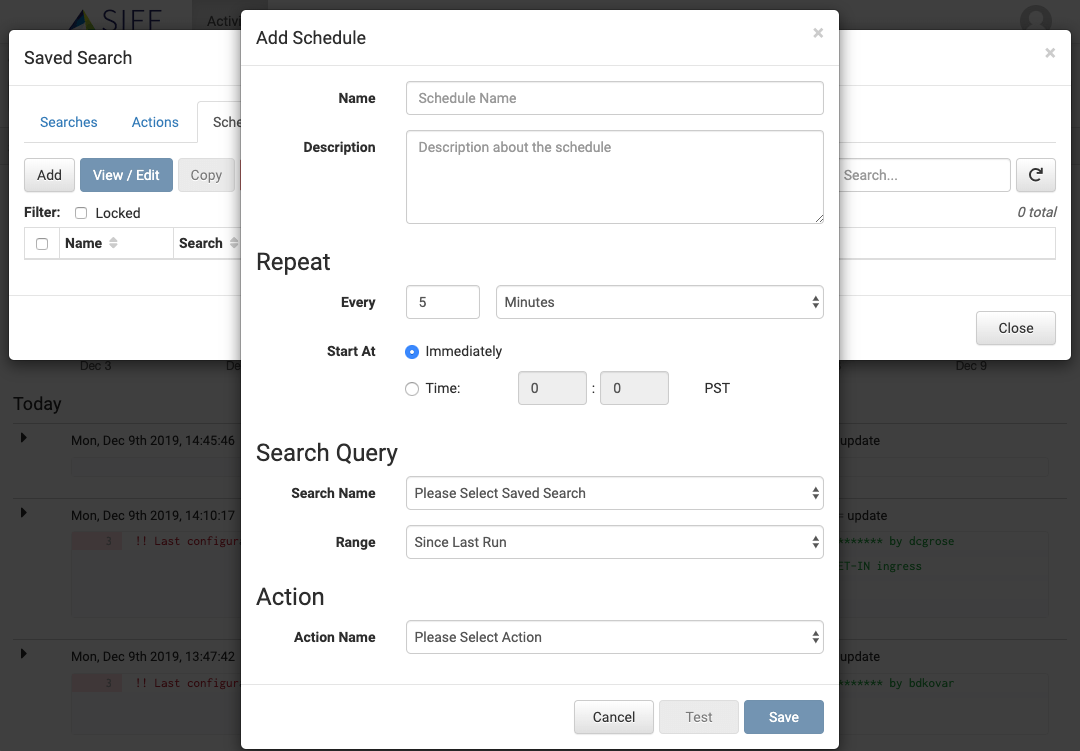
Trigger Saved Searches and Actions
Trigger execution of saved searches and actions by other systems
Dynamically manage devices
Add / remove devices, VMs, containers, etc as they are dynamically added or removed from your infrastructure
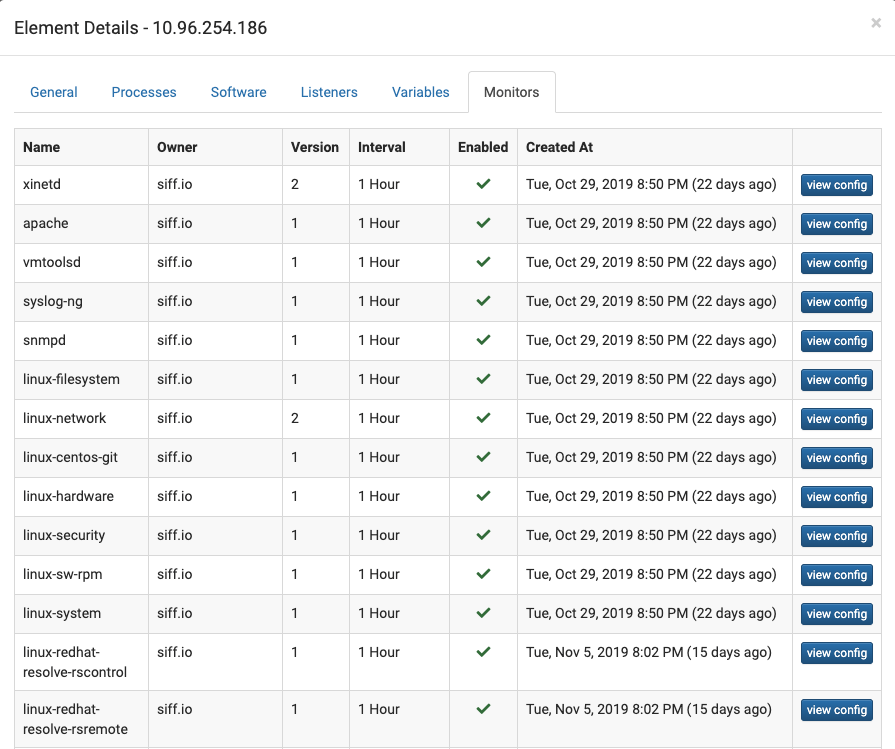
Device and Service Config Discovery
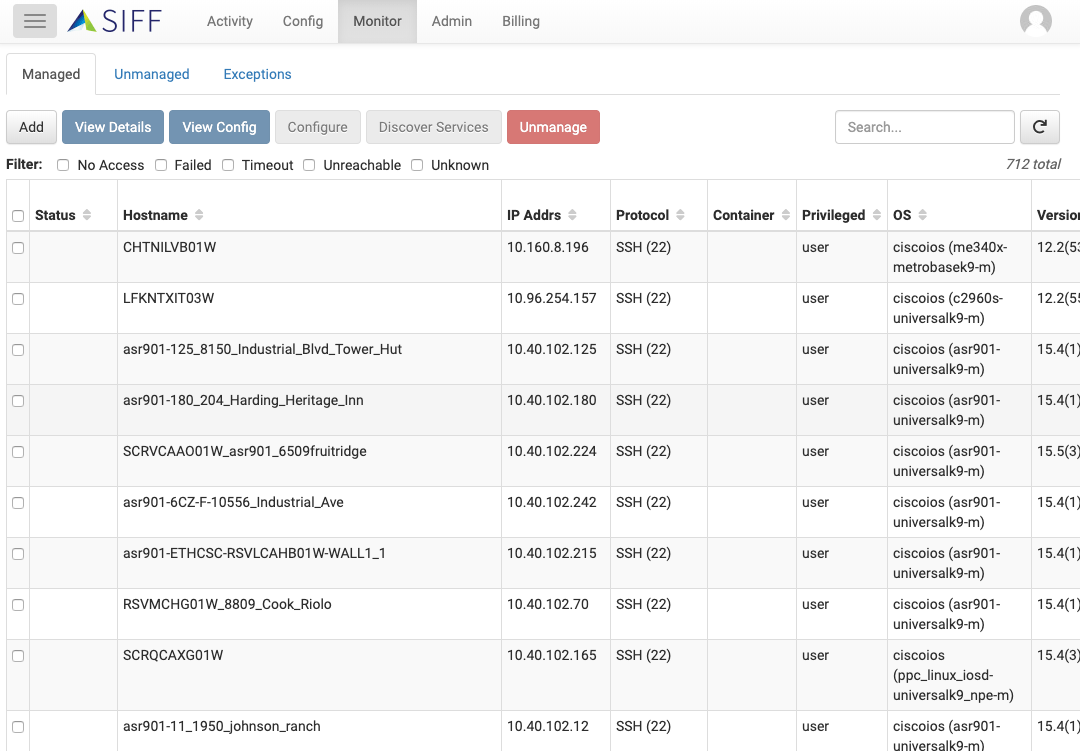
Discovery & Manage Devices
Automatically discover and classify devices
Discovery of IP-based devices on your networks to be managed by the SIFF collector(s). Devices can also be imported from a CSV file
Managed devices and exception lists
Choose exactly what should be managed or excluded
Dynamically manage devices via event-drive API services
Add / remove managed devices for SDN virtual devices, VMs, and containers auto-scaling in dynamic environments
Discovery & Manage Services
Configuration-based Service Discovery
Automatically identify and validate applicable services on your devices for configuration and change monitoring
Automatically support new services and configuration
SIFF built-in Discovery Community Library (DCL) automatically understands new applications and services as they are published to the DCL
Build your own service discovery and monitors
Discover and manage your proprietary custom applications and services with our intuitive Developer UI
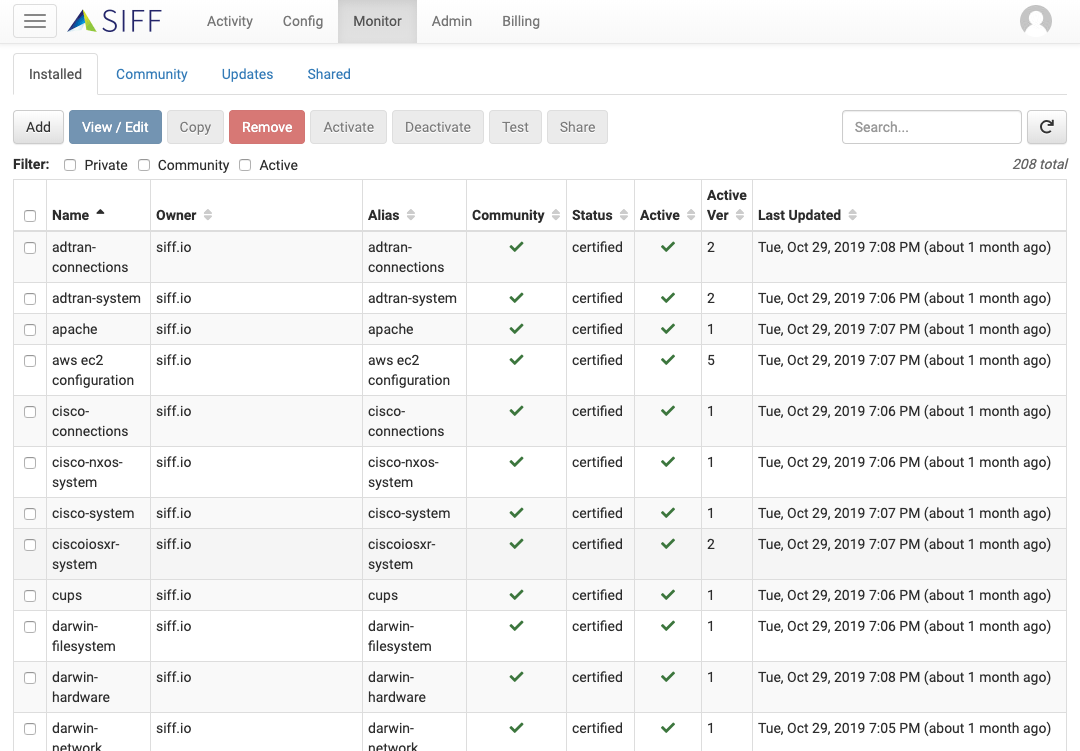
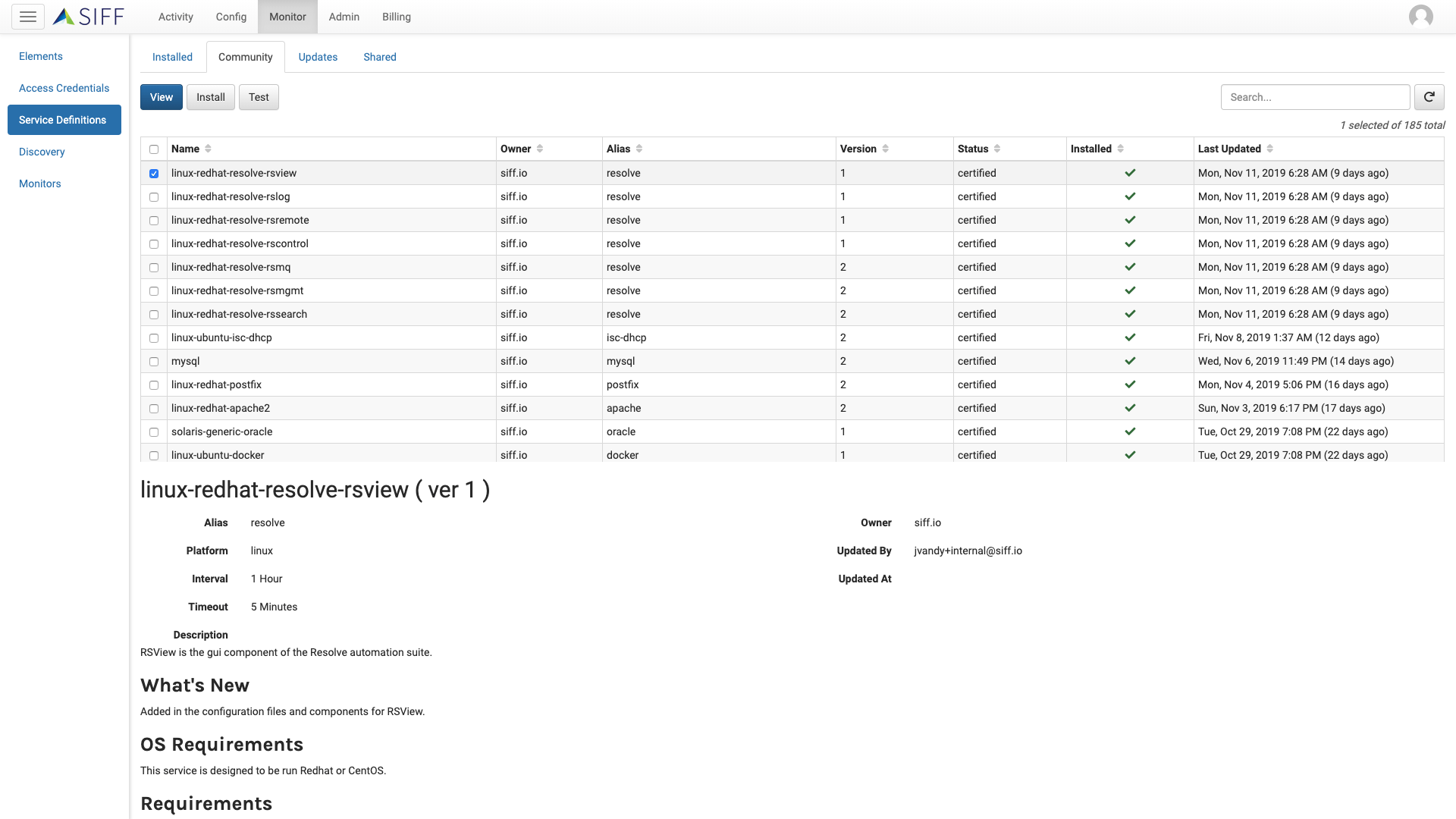
Service Definitions
Large library of auto-installed certified Service Definitions
Automatically discover and collects configuration for certified devices and services. You can also choose to disable or uninstall these certified Service Definitions (SD)
User installed optional community Service Definitions
Users can select and install optional Service Definitions for less common services or pre-certified SDs
Easily update Service Definitions as new versions are available
View and update new SDs as they are published to the community
Additional Custom Monitoring
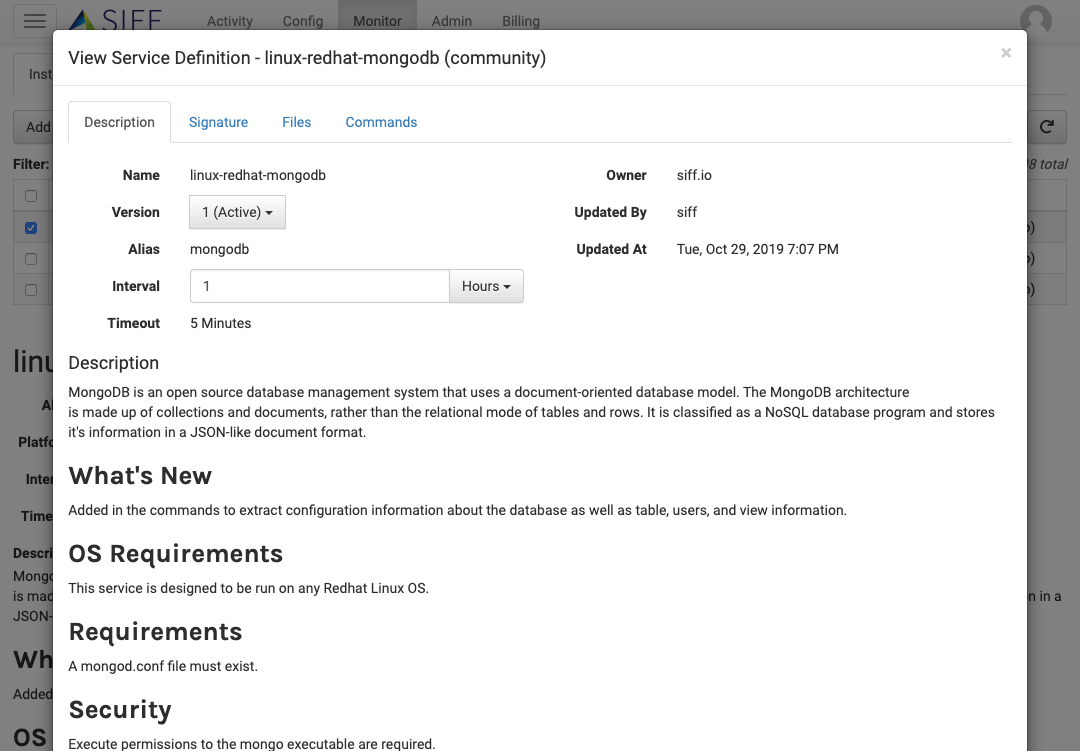
Custom Service Definitions
Customer Services and Applications support
Discover and monitor your own custom applications and services by creating your own Service Definitions
Extend Existing Community Service Definition
Build on top of existing service definitions and share with the rest of the community
Intuitive and no coding Developer UI
Simply list what files to collect and what command outputs to capture. Exclude any content you like to mask out
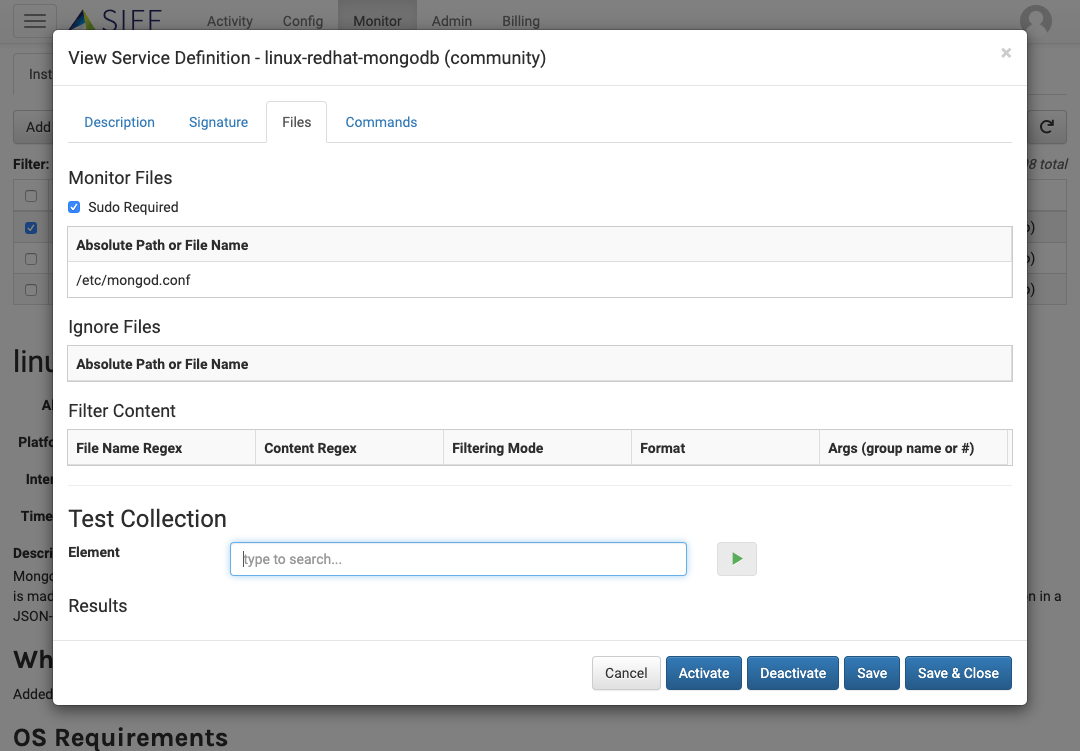
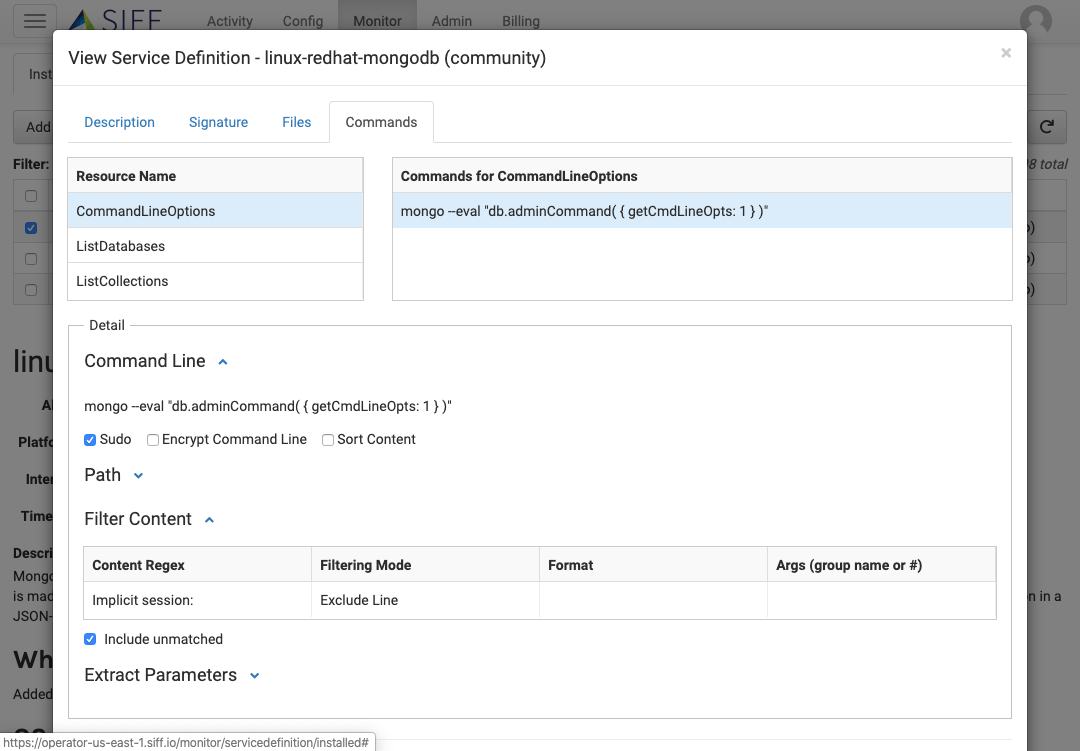
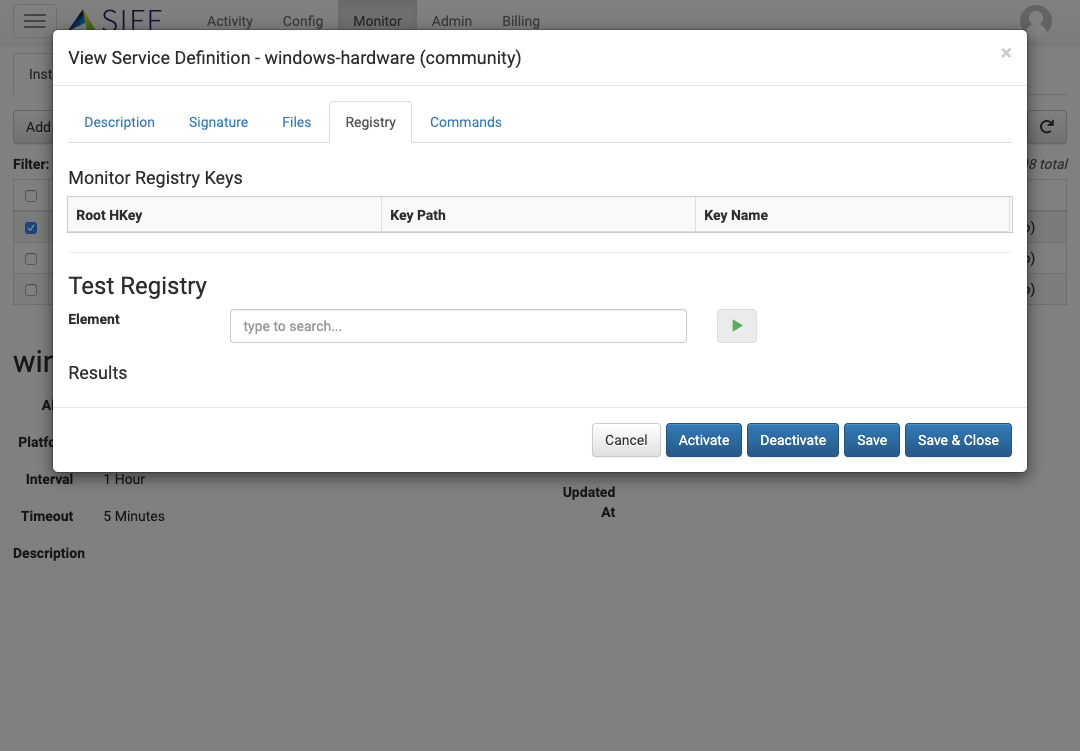
Service Definition - Command Collection
Command Monitors
Define commands to run and capture configuration output. Chain multiple commands together with argument passing for complex sequences of commands.
Mask out content to hide or ignore
Filter sensitive or continuously changing content to ignore
Interactive Testing
Test and verify against your systems before deploying
Content Community Library
Service Definition Library
Browse, install and update Service Definitions from library
Select and install / update Service Definitions directly within the application with the integrated community library.
Share your Service Definitions with the Community
Share your own custom Service Definitions to help others in the community.
Policy Definition Library
Browse, install and update Policy Definitions from library
Select and install / update Policy Definitions directly within the application with the integrated community library.
Share your Policy Definitions with the Community
Share your own custom Policy Definitions to help others in the community.
Forget the complex installs and configs, get started with SIFF Collector in your environment in three easy steps.